Step 1: Create your nao context repository
1. Create a new folder / repository and initialize a nao projectnao_config.yaml, replace your secrets by environment variables
Instead of hard‑coding credentials (service account keys, API tokens, database passwords) in your config file, reference them via environment variables.This keeps sensitive values out of Git, makes it easier to rotate keys, and lets you reuse the same config across local, staging, and production. Example:
GCP_SERVICE_ACCOUNT_KEY_JSON via your deployment platform (for example, as a Secret in Google Secret Manager wired to an env var in Cloud Run).
3. Init a git repository from your context folder
Versioning your nao project in Git lets you review changes to context, roll back safely, and collaborate with your team using pull requests.
It also allows your deployed nao chat to directly sync with the contet in your GitHub repository.
Git Repository Setup
Learn how to turn your nao project into a GitHub repo and follow best practices
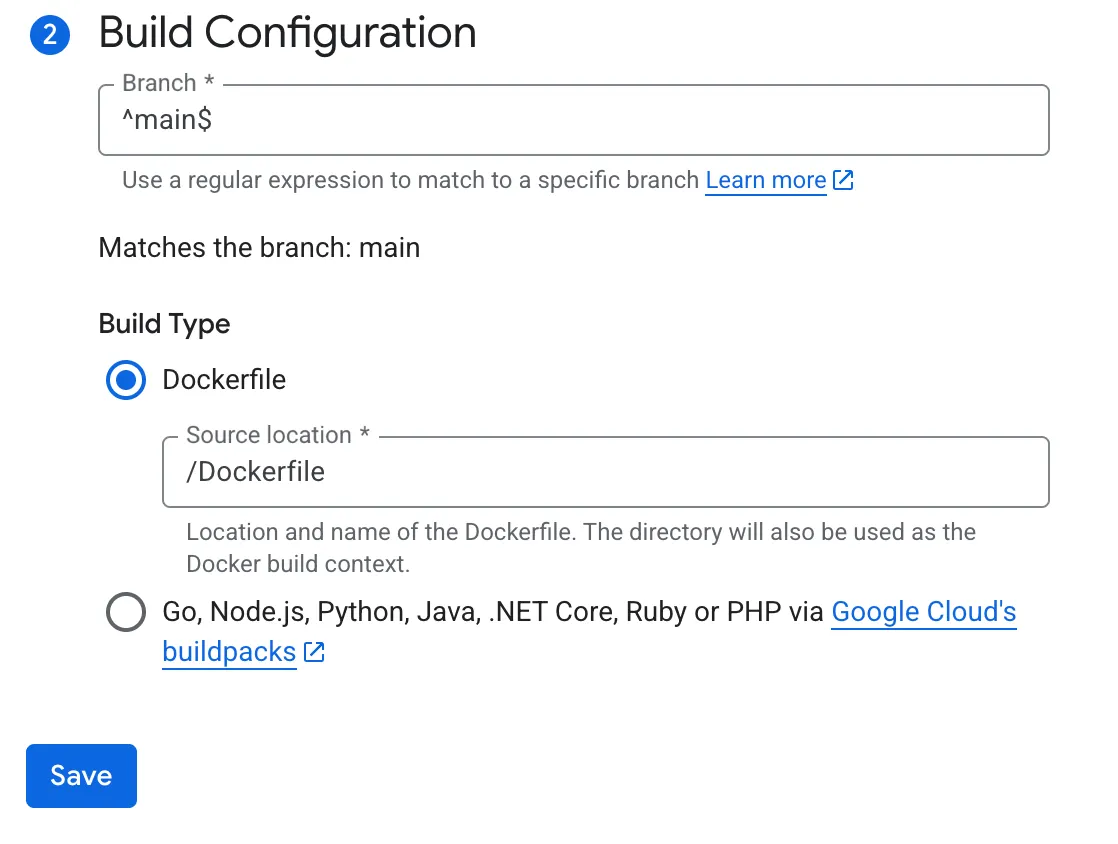
Step 2: Create Dockerfile
Create aDockerfile in your repository, using the official getnao/nao image as the base:
.dockerignore:
Step 3: Create a PostgreSQL database
- Create a PostgreSQL instance - here I’m using Cloud SQL.
- Allow unencrypted network traffic (or configure SSL).
- Enable Private API connections.
- Note your connection string / instance connection name.
Step 4: Deploy nao on your cloud infrastructure
In this guide we’ll use Google Cloud Run as a concrete example, but the same pattern applies to other container platforms (ECS, Kubernetes, etc.).You’ll build a Docker image from your nao project and deploy it to Cloud Run, connect it to a managed PostgreSQL instance (Cloud SQL), and load secrets via Google Secret Manager.
4.1 Configure Environment Variables
Create secrets in Google Secret Manager for all sensitive values:OPENAI_API_KEY/ANTHROPIC_API_KEYGCP_SERVICE_ACCOUNT_KEY_JSON(full JSON content of the BigQuery service account, or other warehouse provider secrets)DB_URIwith your PostgreSQL URI – used for storing your app DB. For example:
- Any other secrets used in
nao_config.yaml(e.g. Notion key)
4.2 Configure Cloud Run service
- Create a new Cloud Run service.
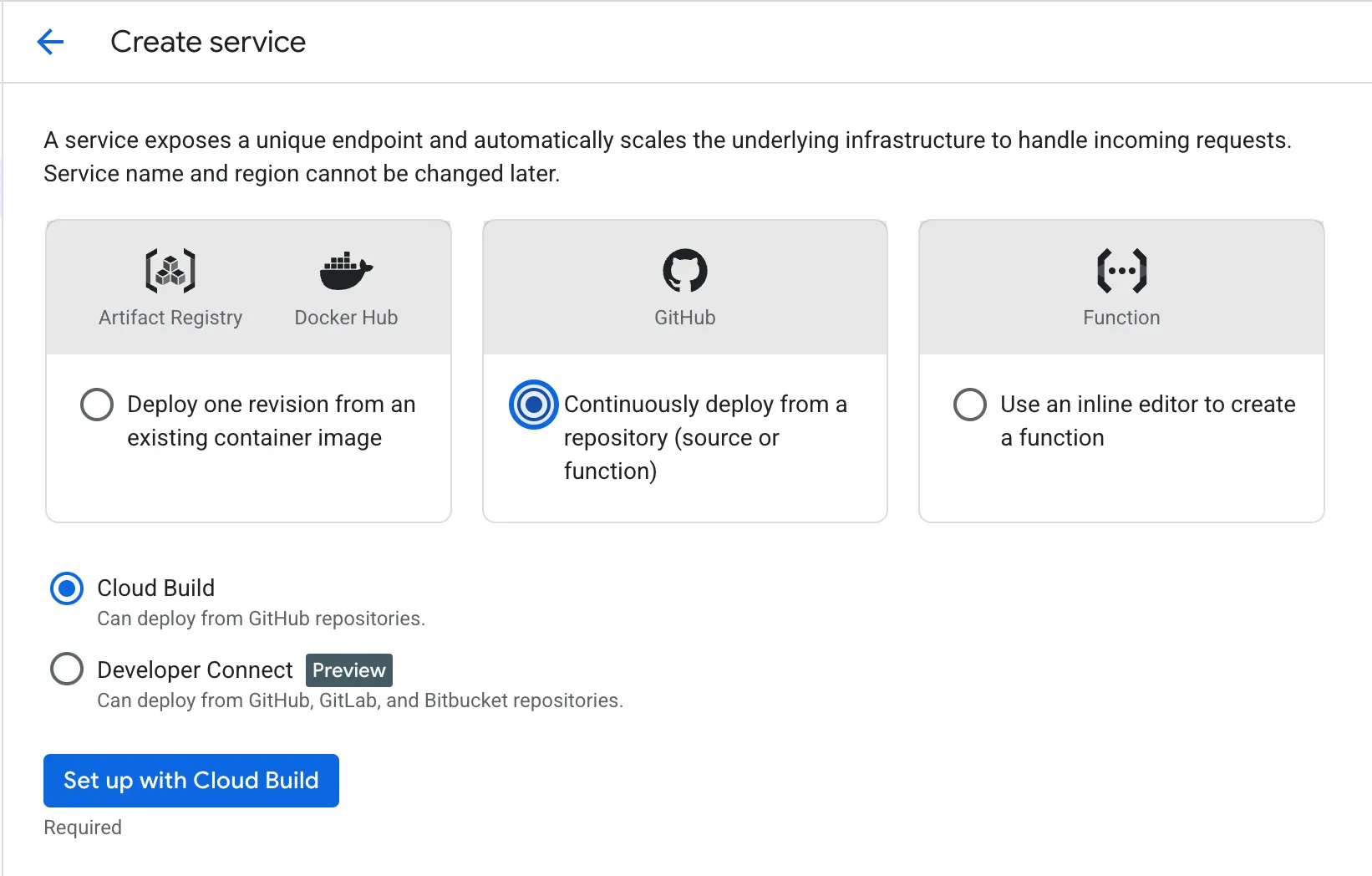
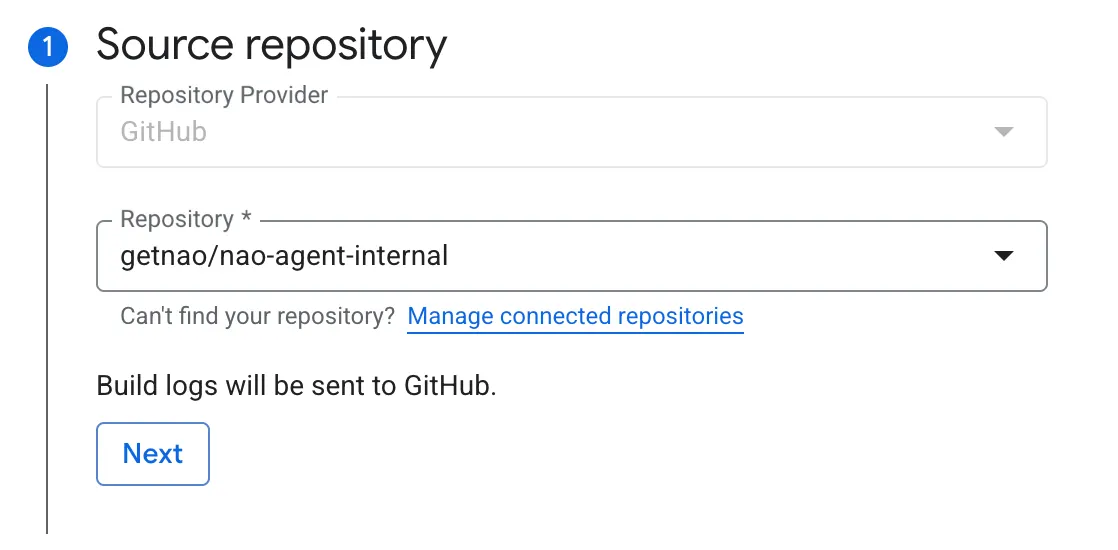
- Use your GitHub repository as the source and set up Cloud Build to build the Dockerfile.
For Cloud Run deployments sourced from GitHub, Cloud Build will automatically rebuild and redeploy on each push to the configured branch.
So your context will always be up to date with the context in the main branch.
- In the service configuration, add these configurations:
5005
Environment variables:
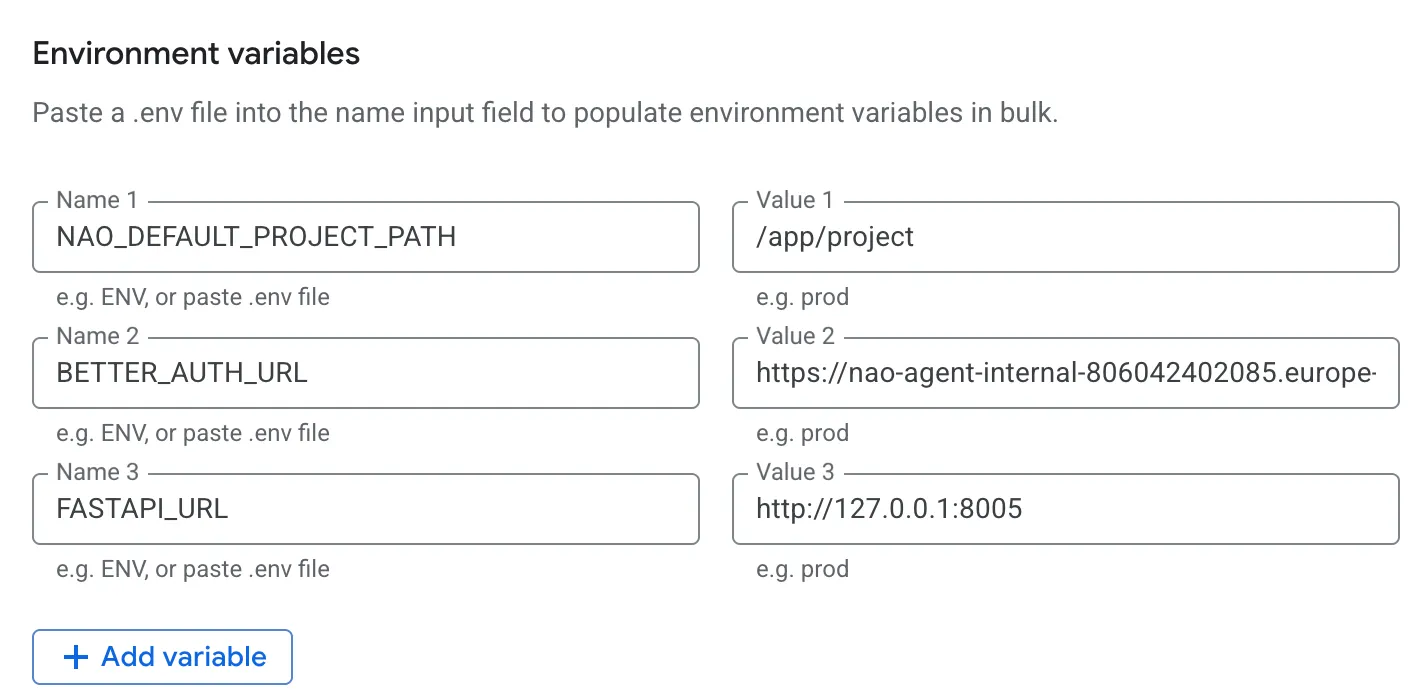
OPENAI_API_KEY/ANTHROPIC_API_KEYGCP_SERVICE_ACCOUNT_KEY_JSONDB_URI
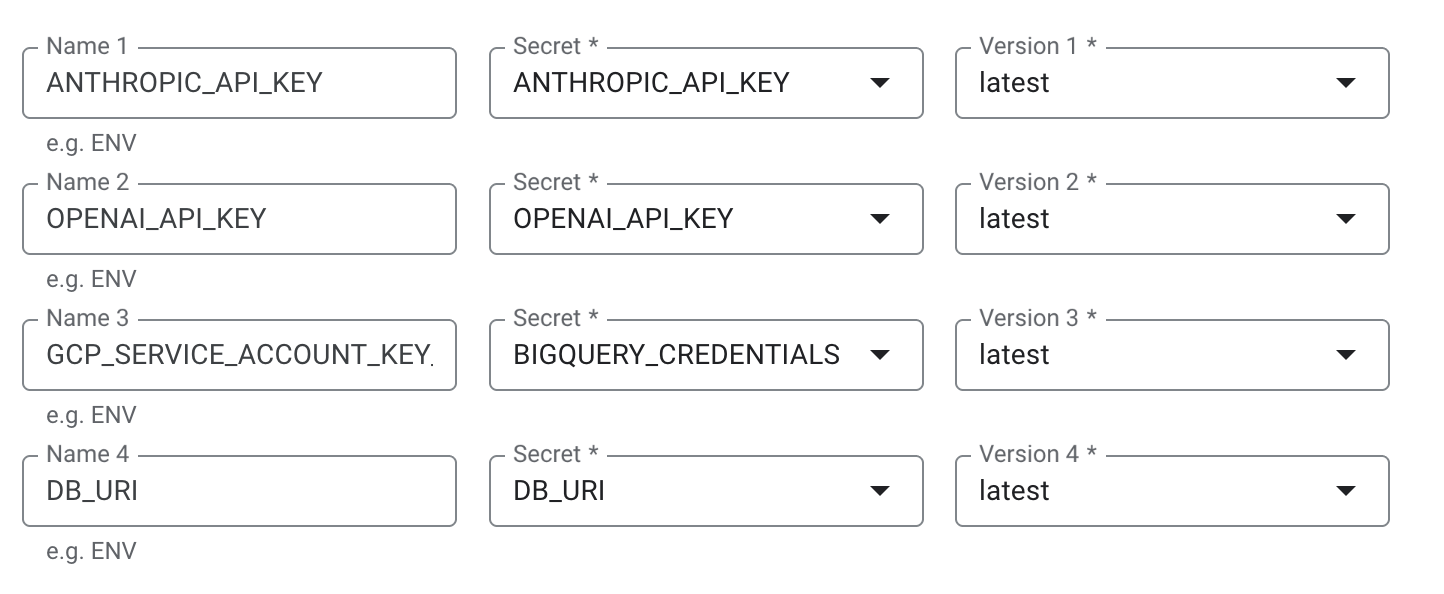
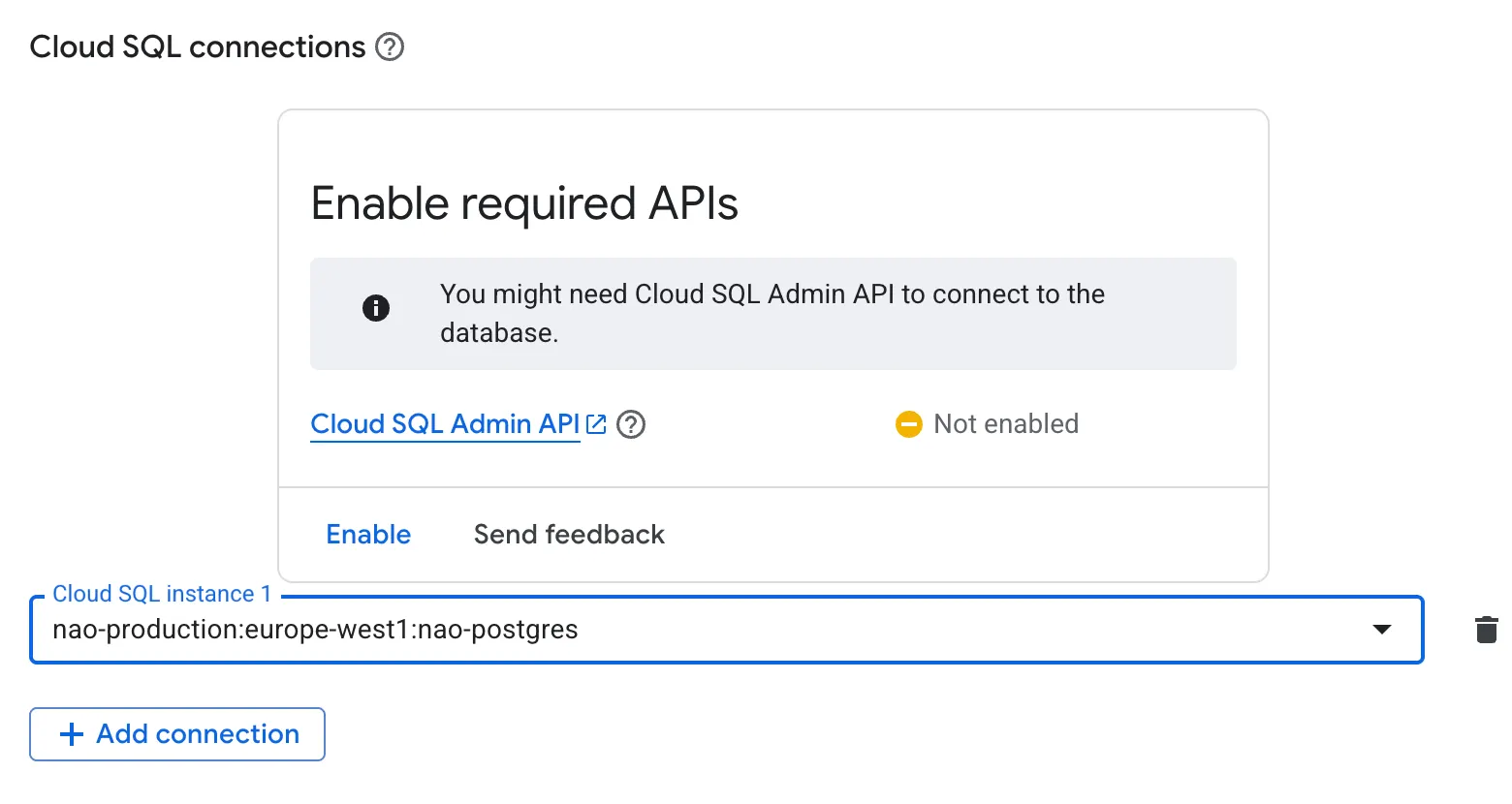
- Add Cloud SQL connection to your PostgreSQL instance.
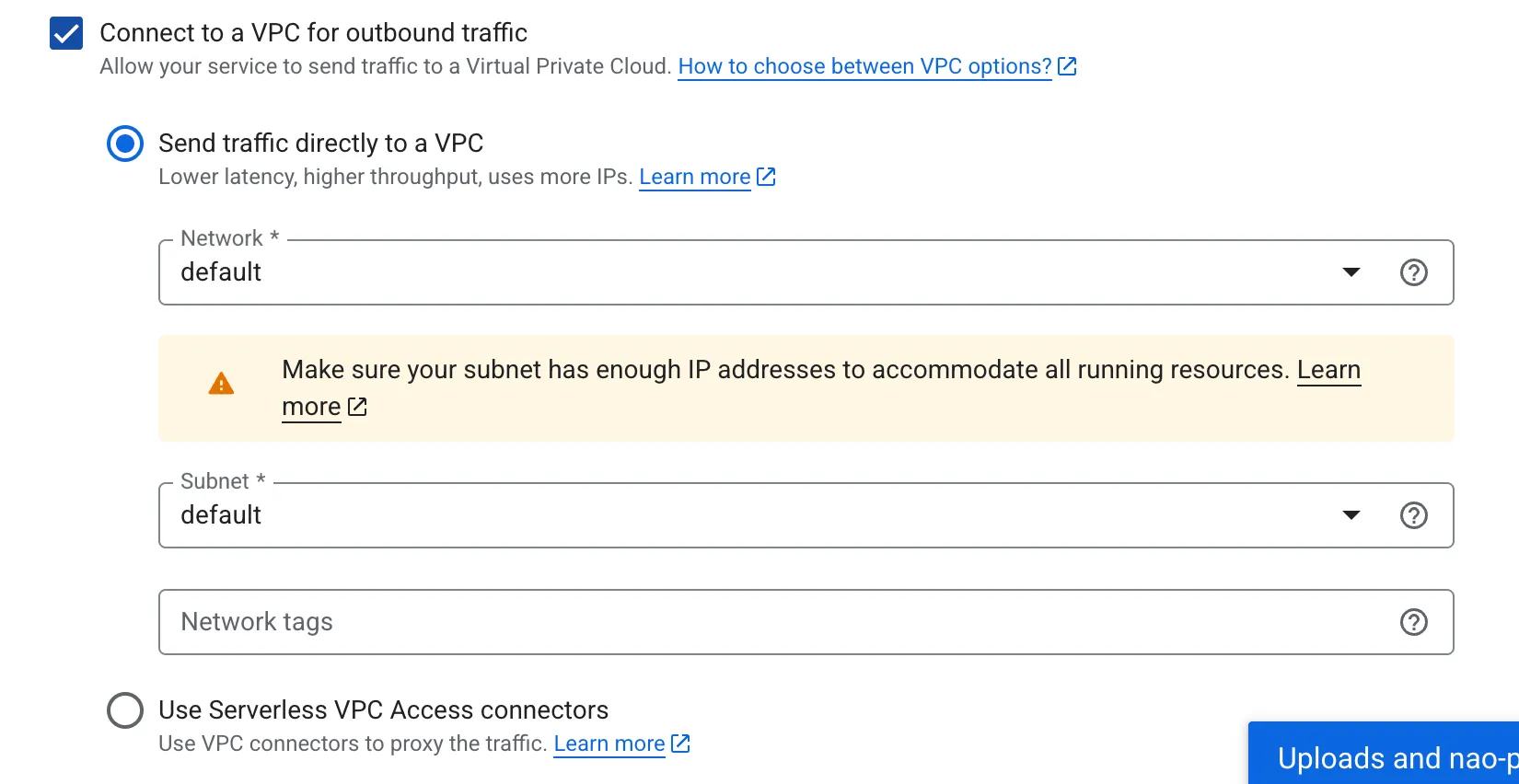
- Activate “Connect to VPC for outbound traffic” / “Send traffic directly to a VPC”
- Deploy the service.
- Once the service is live, copy the Cloud Run URL and update:
- Open this URL in your browser, confirm that the nao chat UI loads, and complete the first sign‑up flow.
At this stage, only the very first user can sign up directly; additional users are added and authorized later via the admin setup and user management flows.
- Map a custom domain (optional)
- In Cloud Run, go to Domain mappings.
- Verify your domain.
- Add the subdomain you want to use (e.g.
sky.naolabs.io). - Add the required DNS records at your DNS provider.
- Update
BETTER_AUTH_URLto the custom domain, for example:
Step 5: Customize your setup
5.1 Add users to your app
Once your chat UI is deployed, invite teammates and manage access from the admin interface.Admin Setup
Invite users, configure authentication, and manage access
5.2 Automate nao sync with GitHub Actions
Automatenao sync so your context stays up to date in Git.
Synchronization
Set up GitHub Actions workflows to automatically sync your context
5.3 Connect a Slack bot
Expose your analytics agent directly in Slack so teams can ask questions where they work.Slack Bot
Connect your deployed agent to Slack channels
5.4 Enable Google OAuth for user sign‑in
To allow users to sign in with Google and control which domains can self‑register:Google Auth Setup
Configure Google OAuth for domain-based sign-up